As the database included actual traffic and details from where the traffic was coming from it was possible to do some digging into in the origins of the redirects.
I settled on one of the referers found in the database as it was still active; oxprxt.tk which at the time of writing has been taken offline (domain does not resolve anymore). However, I will cover what was available and what data that has been collected during the analysis.
The flow which is associated with the referer was "51" and well, its not that impressive in terms of traffic volume, however, since more than 0 exploits launched, it gives the possibility of an infection:
 |
| Flow 51 |
I guess the seller wanted to make sure to keep track on which users that he had sold to, and reading the story about the leak and the posts related to the service it show signs of that it was targeted for sales on one particular forum.
Dive! Dive! Dive!
Accessing oxprxt.tk directly gives a fake webcam chat page. What happens in the background is a totally different thing. |
| First impressions while visiting oxprxt.tk |
 |
| PowerShell Error? |
 | |||
| Fake Adobe Flash Player update page |
So...what happend?
The landingpage consists of a Javascript which is packed and obfuscated. First stage is a reversed, base64-encoded string which reveals another Javascript packed using a variant of the Dean Edwards packer.The page is split into two parts, one being the HTML and redirection, the other an exploit for CVE-2014-6332.
The deobfuscated script shows two different methods for redirecting the victim to the fake Adobe Flash Player page, one being a timeout refresh and the other a click (for the impatient ones):
 |
| HTML and redirection methods |
 |
| CVE-2014-6332 exploit |
So a visitor can be redirected to the fake update page by either waiting more than 3 seconds or click the big "Click to CHAT"-button.
The error generated was due to my VM not having PowerShell installed which made it impossible to execute and download Update.exe. However, that particular file is the same threat that is provided through the fake update page (more on that further on).
The request that was made towards jqueryapi.info is quite interesting as it returns different results depending on the referer, however, the most interesting part is that one of the attempts generated the well-known cushion redirect:
 |
| Redirect cushion <23 chars>.domain.tld |
On the Adobe Flash Player page, a file install_flashplayer16x32_mssd_aaa_aih.exe ( d3014d0391fb9eccfccca288df6e11b8) is offered for downloading. This is one of the many files which reveals itself to be Betabot (details further on).
So, what have been found so far?
oxprxt.tk [VT] - Redirection to fake Adobe Flash page + exploiting CVE-2014-6332.jqueryapi.info [VT]- Works as a rotator.
54.207.49.189 [VT] - Hosting the payload (Betabot) for the CVE-2014-6332 exploit.
Time to poke the bear!
Digging deeper into the server hosting the payload it's found that there is more directories containing files with the same name (Update.exe) as well as a zip-archive named Virus.zip with an executable called Virus.exe.The directory structure when on first visit:
/backend/ateb/Update.exe (d3014d0391fb9eccfccca288df6e11b8) - Betabot - Uploaded: 10th Feb
/backend/ateb/Update.exe (8cbf7cbcdbb24374d60eb95c11a489fc) - Betabot - Uploaded: 17th Feb
/backend/im3/Update.exe (911cfaba8fb33309e9f331ae3ebc5ca4) -Imminent Monitor - Uploaded: 3rd Feb
/backend/Update.exe (e833c258841623fadc2953e09a8f1d60) - Betabot - Uploaded: 3rd Feb
/Virus.zip -> Virus.exe (ce4946e36f82592320ba3a5d0c0e38f2) - Betabot - Uploaded: 8th Feb
/urmom/pl.php - Unknown, keeps loading until timeout is reached. - Uploaded: 29th Oct 2014
/Panel/ - Andromeda Panel
20th Feb a directory called Farhan was created which also included a zip-archive called Virus.zip, including an executable, Virus.exe (93d4053a4a8000ac07eac6cb1d80021e) which also is Betabot.
The Andromeda panel was identified through Virustotal results together with the analysis done by Fortinet:
 |
| Virustotal results |
Prepare to get RickRolled!
All of the executables have one thing in common, which is that they are obfuscated with the same crypter, written in .NET, which limits the amount of victims that might be infected as .NET Framework must be installed.Although the name of the crypter is unknown, it carries a rather interesting message when looking at the strings:
 |
| Link to YouTube playing 10 hour Rick Roll |
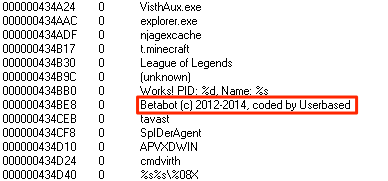 | |
| Betabot strings |
IM is a RAT developed by Shockwave. It's sold publicly on its own website as well as on forums and it seems to be quite popular. As with the crypter mentioned earlier, IM is written in .NET as well and will thereby not run on all systems.
An interesting note is that the IM sample was uploaded 3rd Feb, and on 8th Feb, Genocide (the username assoicated with the RIG flow) posted a thread where he is selling his license for IM:
 |
| Selling IM3 license |
Connecting all the dots and do some visualizing
For this particular case I decieded to use yEd to connect all the entities and create an overview of what have been found during the investigation, this also includes destinations on which the samples communicated.All files mentioned are available on demand.



Inga kommentarer:
Skicka en kommentar